
AMD has unexpectedly reversed its initial decision and released a microcode update to address the Sinkclose security flaw in older Ryzen 3000 CPUs. This follows the company’s earlier announcement that only select newer desktop, mobile, and server processors would receive a firmware update to mitigate this vulnerability. The Sinkclose flaw, officially identified as CVE-2023-31315, is a severe security issue that could allow arbitrary code execution within the System Management Mode (SMM) environment of AMD’s x86 CPUs, a highly privileged operating mode.
Initially, AMD’s decision to exclude older Ryzen processors from the update drew significant criticism, particularly because the Sinkclose vulnerability affects all AMD processors released since 2006. The potential threat of malicious actors gaining ring 0 access to execute code in SMM, effectively creating an undetectable and persistent bootkit, raised concerns among users and security experts alike. In response to this backlash, AMD has now extended the microcode fix to include the Ryzen 3000 desktop CPUs based on the Zen 2 microarchitecture.
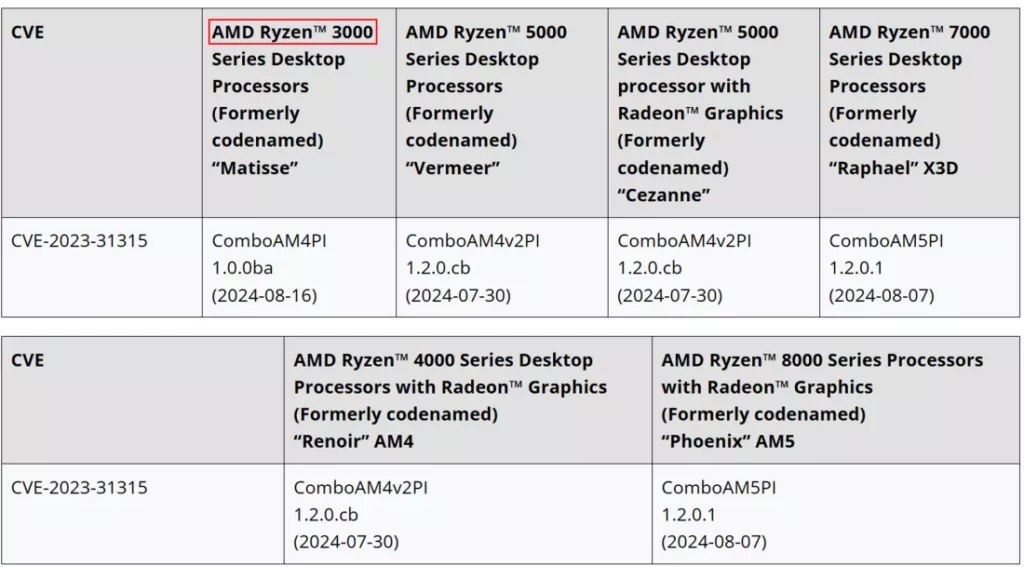
On August 19, AMD delivered the anticipated mitigation, just ahead of the initially planned release date of August 20. PC owners using Ryzen 3000 CPUs should now check for the ComboAM4PI 1.0.0ba update, which OEM motherboard manufacturers are distributing through new firmware versions. This update aims to secure these older processors against the potentially severe consequences of the Sinkclose flaw, ensuring broader protection across AMD’s product range.
This decision marks a significant shift in AMD’s approach to handling the Sinkclose vulnerability, demonstrating the company’s responsiveness to user concerns and its commitment to security.
Featured Image courtesy of Tom’s Hardware
Follow us for more updates on AMD.
